How do I find and manage shadow IT and rogue devices, and put policies in place to ensure we remain secure?
Picture this: your sales team leader excitedly tells you about their new plan to use cloud apps and the latest devices to become more mobile and better reach clients. As the security advisor, your first thought is that more endpoints mean more risk for data security.
With the tools from Microsoft 365, you don’t have to stress anymore. You can analyze the risk of each app used, monitor for login attempts from suspicious devices, and protect sensitive data wherever it travels–all through Microsoft 365.
Don’t let security concerns stand in the way of progress. Give your IT team the tools they need to help the rest of your business thrive.
Defend, protect, secure. IT heroes in action.
The IT professionals in your office do far more than just help you reset your password or recover files from a crashed computer. From the first thing Monday morning onward, these heroes are hard at work protecting your organization.
IT is always at the ready to respond to threats when detected through tools like Windows Defender Advanced Threat Protection and Cloud App Security, all while laying the groundwork to avoid future attacks.
The security features in Microsoft 365 can help your IT heroes perform their jobs more effectively. Give them the help they deserve with tools that benefit your entire organization. Contact us to learn more.
Protect your data in files, apps, and devices, within and across an organization
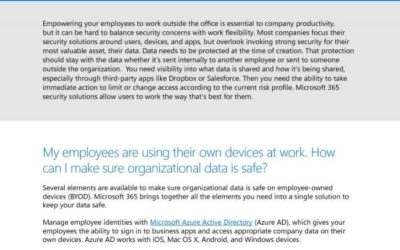
Mobility has become a staple of the modern workplace, offering flexibility to employees and greater productivity to employers. However, this flexibility often requires that employees use their own devices to work when out of office. So how can you protect your data without losing the benefits of “bring your own device?”
Tools such as Azure Active Directory and Microsoft Intune can help you manage access to your data and company networks without invading employee privacy.
At Destek, we want you to get the most out of what technology has to offer. Contact us to learn more.
Azure Strategy and Implementation Guide
Chances are you’re considering transitioning to the cloud for added productivity. If not, maybe it’s time to do so. Destek knows moving your IT to the cloud can be intimidating. That’s why we’re here to help you along your journey.
Azure cloud services can help you to expand the reach of your business using digital channels, anticipate customer needs, understand how your products are used, and quickly develop and improve products and services, keeping your productivity level high.
Contact us to find out more on how we can help you integrate Azure and accelerate your productivity.
Azure ready? Mapping your journey to the cloud.
You need to ensure your data is being properly employed, so your business can stay on task and productive. Destek wants to help you integrate a suite of tools that not only helps you govern your data, but also ensures your workers are productive.
With Azure cloud services, you can adhere to common data models, provide extensibility where needed, and ensure compliance with regulations and standards, so your team can spend more time on what they do best.
Contact us to learn more about the exciting opportunities that Azure has to offer.
Customer Story: BP deploys Microsoft 365 to improve user experience and security
In an ever-changing security landscape, how do you keep users, devices, and data across 80 countries protected? For BP, they use Windows Defender Advanced Threat Protection that can compile information and identify possible threats more effectively than ever before. So effective in fact, that they put it on all 30,000 Windows 10 devices they have deployed across the world.
And this is just one of the many security tools from Microsoft 365 Enterprise E5 that BP is relying on to remain secure as they continue to transform their company. Learn more about their security journey in this video.
Four Productivity Tips for Small Business Owners
Do you have a cloud services provider? If not, you could be wasting time and productivity. Destek is here to help your business adopt the tools you need to maximize your productivity.
Microsoft Azure makes it possible to bring solutions to market quickly and keep your customers happy. By not having to manage servers or virtual machines, you can focus on staying productive.
Increase your productivity with Azure cloud services. We want to ensure you have what you need to succeed. Contact us today.
Alaska Airlines makes shopping easier with Azure and microservices
Productivity is important for every business. At Alaska Airlines, they’re using Microsoft Azure to increase productivity by getting new features to customers faster.
With Azure, you can use the management tools you feel most comfortable with, shorten your development cycles, reduce the risk and uncertainty of releasing software, and enable continuous integration and delivery.
Destek wants you to have the tools you need to keep your business going and your customers happy. Contact us for more information on how to integrate Azure.
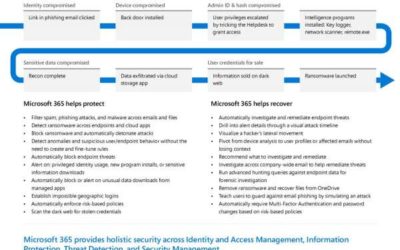
Discover threats quickly, remediate immediately, and mitigate the impact of malware and breaches
A truly comprehensive security system does more than just provide “locks” for the entrances to a network, it searches for and reacts to threats that may have already entered the system.
The Advanced Threat Protection integrated throughout Microsoft 365 monitors and protects everything from data, to endpoints, to user identities. These tools are always working behind the scenes to keep your business secure, keeping you in the loop without overwhelming you with information.
At Destek, we believe in securing your business with a holistic strategy. Contact us to learn more.
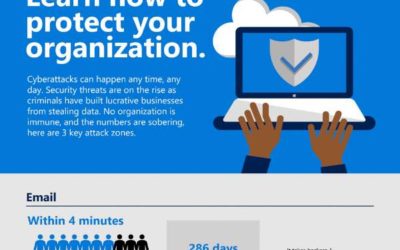
Breaches happen. Learn how to protect your organization.
With a cleverly worded email and one unfortunate click, a hacker can gain access to your system within minutes, and stay there for an average of 286 days before being detected.
How can you avoid this scenario? Check out this infographic to learn about the three most common ways hackers can gain access to your system and the holistic approach Microsoft 365 takes to keep them out.
At Destek, our goal is to keep your business running without interruptions while remaining secure. Contact us to learn more.
Performance and Productivity: Your Guide to Managing Cloud Sprawl
Rethink your approach to managing multiple cloud services and learn how to better safeguard your enterprise with end-to-end security, protect your data, bridge the gap between apps and infrastructure, and change the game with automation and configuration with this e-book. Contact Destek for more.
Move and modernize your Microsoft workloads with Azure
Maximizing your productivity can be tough when you’re working with old IT systems. You need a cloud-based suite of familiar tools that can help you modernize your IT systems. Destek is ready to help you maximize your time.
Microsoft applications and Azure have been built to work better together with flexibility and hybrid capabilities, so you can move to the cloud faster with a growing collection of integrated services.
Your time should be focused on your work, not your transition to the cloud. Let Destek create your seamless transition to Microsoft Azure. Contact us.
A breach is inevitable. How can Microsoft help me detect and respond fast?
With a sinking feeling, you discover your network has been hacked. Questions race through your mind: How did this happen? What have they done inside our network? What information have we lost?
With the right tools, there is no need to panic. Microsoft 365 E5 can help you visualize an attacker’s movement through your system, recommend where to focus your investigation, and help recover files in OneDrive.
Security breaches are never fun, but they don’t have to be devastating. Contact Destek to learn more about how to better protect your business, even from the worst-case scenario.
Customer Story: Guarding university data with a holistic security model
As compared to most businesses, universities have significantly less control over endpoints, such as devices used and the thousands of student user credentials they must give out each year. This makes them especially vulnerable to cyberattacks.
The University of Arizona realized this, so when it came time to overhaul their internal network, CatNet, they prioritized the implementation of a holistic security solution. They found that the solution with Microsoft was uniquely prepared to deliver a forward-thinking security system designed to meet the specific needs of a university.
Even in “risky” situations, effective, holistic security and peace of mind is achievable. Contact us to learn more.
Customer Story: Guarding university data with a holistic security model
As compared to most businesses, universities have significantly less control over endpoints, such as devices used and the thousands of student user credentials they must give out each year. This makes them especially vulnerable to cyberattacks.
The University of Arizona realized this, so when it came time to overhaul their internal network, CatNet, they prioritized the implementation of a holistic security solution. They found that the solution with Microsoft was uniquely prepared to deliver a forward-thinking security system designed to meet the specific needs of a university.
Even in “risky” situations, effective, holistic security and peace of mind is achievable. Contact us to learn more.